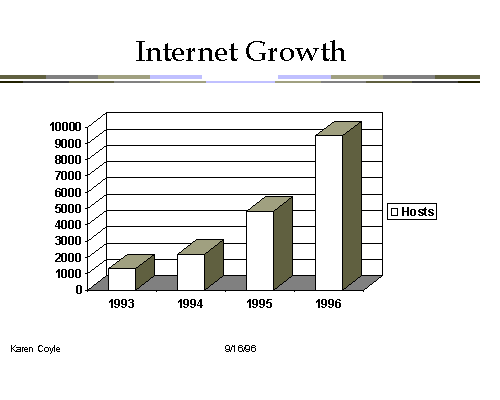
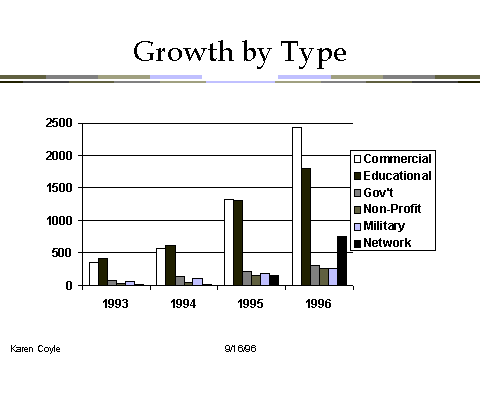
But the Internet is not just growing, it is changing. It began, of course,
as an academic and research network serving primarily the university community.
It also has other kinds of users, such as commercial institutions, government,
non-profit and military. In these key years since 1993, the growth of the commercial
sector has been even larger than that of the others, so that today, there are
more computers from the commercial sector on the Internet than from the academic
world. This is an important change - a change from its academic origins to a
commercial and possibly a consumer-oriented network.

Note also that there is a large growth in 1996 of the computers in the "network" component. These are the people who in the business of creating the Internet infrastructure. They are in the business of being online and getting other people online. This is clearly a growth market.
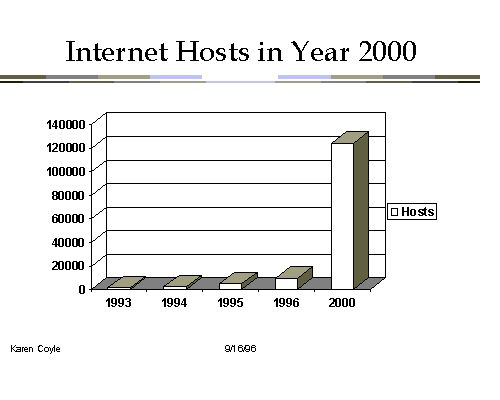
In case you have the feeling that you are getting onto the Internet late,
look at the same range of 1993- 1996 when placed alongside where some people
predict we will be in the year 2000. At our current rate of growth there will
be from 100 to 125 million computers connected to the Internet by that year.
From this perspective, 1996 is the ground floor.
 July 3, 1995 issue of Time magazine, with its cover story entitled "CyberPorn."
For many people in this country, this left a lasting impression of the Internet,
and that impression is that the Internet is nothing but SMUT.
July 3, 1995 issue of Time magazine, with its cover story entitled "CyberPorn."
For many people in this country, this left a lasting impression of the Internet,
and that impression is that the Internet is nothing but SMUT.
The article cited a study done by a graduate student at Carnegie Mellon University. Within a few weeks of the appearance of this story, savvy members of the Internet community had proven that the study itself was flawed, perhaps to the point of being fraudulent. The student who authored the study is no longer in the graduate program, and the Time reporter has lost his credibility among Internet users.
Naturally, Time didn't report this debunking of its story with the kind of publicity that the story itself received, so many people were left with a flawed impression of Internet content.
Let's talk about the reality of the Internet and pornography. Is there sex on the Internet? Yes, there is. There is everything from adult bookstore type materials, to the airbrushed centerfolds of Playboy and Penthouse. There is also a wide variety of other materials relating to sex, from medical information on sexually transmitted diseases, to support groups for people with HIV, to discussion areas for teens who are confused about their sexual identity.
And there are other types of controversial materials on the Internet that some of your patrons might find objectionable. An interesting example that came recently was that of white power sites. There are groups advocating "white power" who place their information on the Internet. One organization called for the censoring of them, calling their sites "hate speech." What followed was an interested and often heated discussion on the Internet of the questions of censorship and the true meaning of the First Amendment. The white power sites remain online.
There is also Dianne Feinstein's famous, or infamous, "bombing making recipes." At least twice now she has introduced bills in Congress that would make it illegal to disseminate information on bomb-making over telecommunications systems. The is unswayed by the fact that this same information is available in print - you might even carry some of it in your libraries. As a matter of fact, some of it is available from the US Department of Agriculture.
You may have understood by now that computers, unfortunately, have not given humankind any new ideas. There is nothing online that you can't also find off-line, at least in terms of ideas, beliefs or facts.
So how should libraries handle the controversial material that can be found on the Internet? The American Library Association has prepared an interpretation of the Library Bill of Rights entitled: Access to Electronic Information, Services, and Networks: an Interpretation of the LIBRARY BILL OF RIGHTS. In short, this document advises libraries that they should treat online information just as they do hardcopy information in their libraries. And that all information is to be considered constitutionally protected speech unless decided otherwise by a court of law. And only the courts can make that decision.
The rule interpretation of the Library Bill of Rights also reminds librarians that ALA policy is that we do not discriminate against our patrons based on age; that our young library users have the same rights to information as do adults.
There were a number of problems with the CDA, not least of which was the fact that it made some materials illegal in the online world that perfectly legal off-line.
President Clinton signed the CDA on February 8th, and within hours of his signing, that very day, the ACLU presented a lawsuit that challenged the constitutionality of the portion of the Telecommunications Act. Less than two weeks later the American Library Association and twenty other organizations filed their own lawsuit, which was then combined with that of the ACLU.
The ALA lawsuit is a marvelous document, something you can't usually say about legal writing. And this is one of those moments when I am extra proud to be a librarian. Because ALA understood that what we have here is in information problem, and they set about to provide that information. The fact is that the vast majority of our elected officials and most of our members of the court are not online. They have not used email, they have not surfed the Net. Yet they are making decisions about this new medium.
The first part of the ALA lawsuit is the best plain-language explanation of how the Internet works and why censorship over the Internet won't work, that I have ever seen. And the best part about it is that the ALA strategy was successful. By the end of the hearings the judges had learned a lot about the Internet. In their decision they included an equally clear explanation of how the Internet works, which has now been sent to the Supreme Court for final decision on this matter. In this way, the Federal court judges are educating the Supreme Court judges in this important technology.
Let me give you some examples of the arguments against censorship of the Internet.
The Federal court in Philadelphia found the CDA to be unconstitutional. The question has been passed up to the Supreme Court now. It is on a "fast track" and should be heard by the end of this year. You can follow this on ALA's Web pages at http://www.ala.org.
These programs were originally aimed at parents, and the proper place for this filtering to take place is in the home. There is however a great deal of interest in these programs today on the part of employers who would like to make sure that their employees are not spending the day surfing the sports sites or reading virtual playboy.
Using these programs in libraries is not recommended. Among other things they take the selection process away from the library and put it in the hands of a company that does not have the same goals as a library does. But you may find yourself having to defend your decision not to use these programs, or to at least argue against their use. And your library may have to resort to filters to make the Internet acceptable to your community. In either case, it is important that you understand some of the pitfalls of using a content filter.
Most filters work by blocking access to a list of Internet sites. Because new content is constantly appearing on the Internet, there is no way users could keep up with this "forbidden" list. So the software vendors present their product as a service with regular updates of the list. Some products have a "permitted" list. Some filter based on patterns of incoming keywords.
The most important thing to know about these filters is that they are not perfect. You cannot guarantee that your patrons will not encounter material that they find objectionable. The filter may have missed a site, or a retrieved site may be too new to have been included in the list of information to be blocked. In addition, the definition of "appropriate" that is used by the filtering software may not be the same as your patron's. And since any library's patrons will have a wide variety of definitions of appropriate, it will not be possible to please them all.
The filtering used by these programs filters whole Internet sites, not single documents. This means that they block access to some appropriate materials at sites that may have a small amount of inappropriate content.
There are a number of stories about filtering gone awry. One of the first that I heard was from Carnegie Mellon University, where they decided to block all of the Usenet groups that were in the hierarchy "alt.sex." Some of the most sexually explicit discussion takes place in this hierarchy, it's true. But it also includes the discussion forum "alt.sex.not," possibly the only place on the Internet where there is a serious discussion of the advantages of celibacy.
Another story comes not from the Internet but from American Online, yet it is a good example of how hard it is to judge content using a keyword method. At one point, America Online banned the use of the word "breast" on their service. They looked very foolish when this made it virtually impossible for the Breast Cancer Survivor's Support Group to continue functioning, and they even got some angry notes from users in their Cooking Forum.
One service banned access to the White House web page for a short time. It turns out that there was one page that included photos of the first and second families, and the caption on one of these photos included the word "children" while a caption on another had the word "couples." It turns out that this combination of words was a red flag for that filtering service indicating a possible child pornography site. This is also a good example where one suspect page causes the blocking of a whole site that has a lot of valuable and appropriate information.
The fact is that the computer screen, with its colorful graphics, catches people's eye the way a paper page does not. Not only may some patrons be exposed to content they might find offensive, it's important to think about the privacy needs of the person using the Internet. After all, that person might be accessing information they aren't comfortable with in a public setting, like certain embarrassing medical topics.
We don't guarantee total privacy for our patrons in the library - their searching of the OPAC can be viewed by others, for instance. But in general we are sensitive to the private nature of patrons' information requests. Most likely you will be shoe-horning the Internet computer into an already crowded library, but it is important to think about the issue of privacy when placing the machine. In addition, there are screens that can be used that help block the screen from accidental viewing by others, thus "protecting" other patrons from being exposed to displays they would find offensive or disturbing.
Transactions can also be recorded on the Internet. Though the World Wide Web looks seamless to the user, every time you click on a link, you are making a connection to another computer on the Internet. In essence, you are contacting that computer and asking it to return some information to you - to your computer. For this to happen, your computer has to identify itself to the computer at the other end of that "click." This is done through a system of numbers not unlike telephone numbers: every computer on the Internet has a number that identifies it. The other computer can log transactions much like the phone company does, though at the receiving end. It can keep track of the numbers of the computers that contact it, what files they ask for, along with the date and time. So every time you click you are leaving a record of your activity.
This sounds quite frightening, but let me remind you that these transactions don't log who you are, as a person, they log the address of the computer - because as far as the Internet is concerned, there are no humans involved, just computers. Since many people will use the library's computer, you are providing a relatively anonymous access for your users. Here is an example of some log information from my Web site. As you can see, it reveals only a small amount of information about the user activity.
citytel_prct4.citytel.net - - [25/Aug/1996:22:41:39 -0700] "GET /~kec/sfpltalk.html WWW.FHD-Stuttgart.DE - - [26/Aug/1996:03:55:46 -0700] "GET /~kec/sfpl.html host06.net.voyager.co.nz - - [26/Aug/1996:04:22:25 -0700] "GET /~kec/ethics.html 164.58.86.51 - - [26/Aug/1996:07:25:39 -0700] "GET /~kec/libcens.html
Why are the logs kept? Most sites keep logs of accesses so they can gather basic statistics on how often their site is accessed, which documents are accessed most often, etc. Many sites then erase the logs, perhaps monthly or weekly, and start over. Logs can also be used if the computer system experiences some trouble, because they give a record of what was happening at the time. The logs are also what is used to catch hackers who are breaking into their system. In theory, if a library patron hacked into a top secret CIA computer from your library's computer, diligent FBI agents could trace the break-in to your computer at a certain day and time. This doesn't happen often!
But as you can imagine, advertisers are not quite content with simple numbers of accesses. They would like to know more about the actual humans who visit the site - more about their demographics. And they'd like information on repeat visits by the same users. They can't get this from the logs because the people are hidden behind these uninformative Internet addresses.
So some sites use the trick of "free registration" to gather more information about people. These sites won't let you in until you sign up with them. They usually ask for at least a name and an email address, though sometimes they also ask for a street address and phone number. You then pick a password and have to sign in each time you want to visit that site. This way, they know how often you return, what you view, etc.
Individuals using the library computer can register with these sites because it is unrelated to the computer itself or the Internet account. So it's important that you educate your users about the privacy implications of this. The main question is: do you know who you are giving this personal information to? In most cases, you do not. And in the real world most of us would be reluctant to give any personal information, even our names, to a complete stranger.
You also don't know what use will be made of the information. Some sites promise, on the sign-up page, that the information you provide will not be sold (like a mailing list) or given out to other parties. But you still don't know what use WILL be made of it.
There may be situations in which a patron does want to give out personal information and feels safe in doing so. For example, you may have a patron who is researching new cars and is willing to sign up with the General Motors company site, knowing that he or she may be in for a new round of junk mail at home. Adults can exercise this type of judgment once they understand the situation. Children need more guidance.
There is a wonderful pamphlet, available both online and in paper copy, called Child Safety on the Information Highway, that is put out by the National Center for Missing and Exploited Children. It is aimed at parents and gives them a brief and simple set of guidelines to use with their children. We teach our children certain rules to use in the real world, like don't get into a car with a stranger, don't give out certain information over the telephone. This is the same kind of rules, but for cyberspace. It is a great document to give to parents who are uneasy about letting their children use the Internet because it is something they can DO to help protect their child. It also isn't a bad idea to have this near your Internet machine for all adults to read, because the advice given here for children, and the explanations for the parents, also works for adults online.
The answer is yes, but a qualified yes. The Electronic Communications Privacy Act of 1984 legally protects your private communications, such as email. But we know that legal protection is not the same as real protection, and the fact is that the technology does not prevent anyone from reading your email messages.
On each computer system there is someone, usually called a "system administrator," who can access every file on the system. They need this capability as part of their job. As far as the computer system is concerned, an electronic mail message is just another file. Someone who hacks into a computer can often read private files, such as email messages that are stored on the computer. Also, email messages can be misdelivered. And email has been turned over to courts in a number of cases involving computer crime and even personnel disputes.
Now the fact is that nearly all of the time your email messages are read only by the intended recipient. But you should always remember that email messages are "in writing" and they may be stored on a computer or in backup files for an indefinite length of time. You should be cautious about putting anything into an email message that would really embarrass you to death if it ended up in the wrong hands.
There is one important exception to email privacy, and it affects nearly all of us - you do not have a guarantee of privacy when using a computer or account supplied by your employer. Your work email messages legally belong to your employer, just as memos and letters you write on company or institution letterhead do. Your employer can "spy" on your email messages, even without warning you.
For this reason, it is absolutely vital that every library have a clear policy on employee use of email and of the Internet over the library's account. Because email FEELS private and most employees will not know that it isn't unless a policy is in place that informs them. It's also a good idea to spell out what the library sees as acceptable use of work email accounts. Can you send email to Betty at another branch to arrange a non-work lunch together? Can you participate in library-oriented discussion groups on the Internet? Non- library oriented groups? All of this needs to be made clear before libraries and employees find themselves in an embarrassing position.
There's a popular expression on the Internet that "information wants to be free." This was definitely the spirit of the early Internet users who were mainly working in academic and research institutions and who developed the Internet expressly for a free exchange of information. Until quite recently, almost no one bothered to put copyright notices on their Internet materials, and even now a copyright notice isn't very common.
But the fact is that the intellectual property laws apply to online works just as they do with works in hardcopy or other media. Materials on the Internet are copyrighted by virtual of having been written by someone, regardless of whether there is a copyright notice on the piece. This is something that many Internet users do not understand - that because the information or documents are being made freely available does not mean that they don't belong to someone.
Fair use applies to online materials, so your and your library users can print a copy of a Web page for personal or educational use, just as they might make a photocopy of a magazine article. They can copy it to diskette to take home for further viewing.
What they can't do is also the same as what they can't do with hardcopy materials: they can't copy something down off the Internet, put their own name on it and call it their own. They can't take materials off the Internet and publish them elsewhere, even if it's not for profit.
In addition there has developed a kind of etiquette about using Internet materials where the analogy to the offline world doesn't hold up well. It is considered impolite to send a message or a document written by someone else to a discussion group or other large number of Internet users without first asking the author.
The good news is that in the online world, it is often very easy to ask the author for permission. Almost every World Wide Web page has on it the email address of the author or person responsible for the page. It's been my experience that if you contact these people they respond quickly and are often very generous about allowing their information to be used.
There is one area, though, where we do have a bit of a problem with copyright on the Internet, and that is when it comes to images and sounds.
Before the World Wide Web there was a text-based online system called Gopher that some of you might remember. The user interface for gopher was simply menus; lists of topics or documents that one could select from. When the World Wide Web came into being, we suddenly had the ability to include graphics with our information. This is great unless, like me, you are totally artistically challenged. The first time I put together a Web page I decided I wanted a little back-arrow icon on it, so I created one with my simple drawing program. It shouldn't be all that hard but my arrow wasn't even recognizable, much less aesthetic. So I did as everyone else does on the Internet and I found a nice back arrow on someone else's page and stole it.
This theft of icons, colored buttons and nice bars and dividers is quite common and generally accepted. Or it was. But now we have on the Internet people who put much more elaborate graphics on their pages, which are just as easy to steal. And some of these pages belong to companies who have actually commissioned graphics from professional artists. Some of these graphics contain logos and trademarks.
Copying and using another person's graphic is not fair use. And companies on the Internet are beginning to crack down on what they see as misuse of their graphical materials.
Fortunately, there is hope for those of us who don't have any artistic ability. There are many collections of small icons, buttons, and bars that are made available so that we can have decent-looking Web pages. The InfoPeople Web site lists a number of these, and others are available through services like Yahoo (just search on the word "icons").
There's something else that I should briefly mention about copyright: there has been a proposal for a revision to the copyright law to further protect works in the online environment. Many of us are concerned that this revision would make it difficult for libraries to disseminate digital information because it places restrictions on lending and fair use. The American Library Association is part of a group called the "Digital Future Coalition" and you can follow developments in this area on either the ALA or the DFC home pages. My home page also contains a piece I've written on the proposed changes to the copyright law.
The NII program is being managed under the auspices of the Department of Commerce. Yes, Commerce. Not Education, and not the Library of Congress. Though the word "information" is in the name, the NII is business, not education. And the "Agenda for Action" makes it very clear that the Federal government will not fund nor build the NII. Instead, it will be built by the commercial sector.
This is why we see players like Viacom, MCI, Disney, Time/Warner, Microsoft and others involved in the development of the Information Highway. And believe me, they aren't getting into it so they can disseminate local bus schedules or income tax forms.
From the beginning, one of the stated goals of the NII was that of universal access. Yet, true to their "hands off" approach, the Federal government is not planning on funding universal access.
I'll admit that this gets me angry at times. I was pretty upset when Clinton and Gore flew out here for their photo-op during NetDay96. The money that it cost for their trips out here in Air Force 1 and 2 (because they aren't allowed to "plane pool" of course) would have funding Internet access for a number of California schools that now have wiring but have no computers and no Internet connection.
But the reality is that Federal funding will be scarce. So if it feels to you at times like libraries are being left to bootstrap their way onto the Information Highway, you're right - that's exactly how it is. And as unfair as that might seem, I want to tell you that getting onto the Information Highway, as you are doing today, is the most important thing you can do.
Sometime in the future - five years, ten years from now - we will have a highly elaborate online system going into most homes in this country. And that system will deliver games, entertainment, and some Infotainment. It will not deliver the kind of everyday information that we know so well from the reference desk. One thing we librarians know that most other people in this country don't is that of all the information in the world, much of it has no commercial potential. And the Viacoms and TCI's and Time/Warners are not going to be carrying it.
By getting onto the Internet today, you are reserving a place for the public library in the digital future. And you are reserving a place for those information services that are so greatly needed by members of the public but that won't make any profit for the media companies of tomorrow. The only way that we will have a true National Information Infrastructure is through our public libraries. I hope you can remember this on those days when you are feeling over-worked and under-funded.
